MGS+ Security Data Services – MGS+ Report
This service is specifically designed to deliver well defined deliverables into critical intelligence demands of our client.
These critical intelligence demands are across Technology Information Data Positioning Planning and Execution.
Client Intelligence Technology Information Data
client understanding of Intelligence Technology and Intelligence Information and Intelligence Data
client leverage of technology to process information relating to aspects of their operational environments
client use of information to contribute to their decision-making process; provide reasoned insight into future environments; increase information utility
Client Intelligence Positioning
client capability in anticipation and prediction of future environments and better defining differences in available courses of action
client depth of quantitative analysis and qualitative judgment and competing interpretation
client continuous examination of their intelligence needs
client definitions of goals, frameworks, quantifiable outputs and objectives
client focus on actionable intelligence creation
Client Intelligence Planning Execution
client types of intelligence – Warning; Current; General; Target; Scientific Technical; Counterintelligence; Estimative; Identity
client levels of intelligence – Strategic; Operational; Tactical
client principles of intelligence – Perspective; Synchronization; Integrity; Effort Singularity; Prioritization; Excellence; Prediction; Agility; Collaboration; Fusion
Definition and Terms Details:
Intelligence: Technology Information and Data
Technology enables access to, in near-real-time, very large amounts of information relating to aspects of the operational environment (OE)
Information is of greatest value when it contributes to the decision-making process by providing reasoned insight into future conditions or situations.
Raw data by itself has relatively limited utility. However, when data is collected and processed into an intelligible form, it becomes information and gains greater utility.
Intelligence
Ultimately, intelligence has critical features that distinguish it from information.
Intelligence allows anticipation or prediction of future situations and circumstances, and it informs decisions by illuminating the differences in available courses of action (COAs).
Intelligence is not an exact science; intelligence analysts will have some uncertainty as they assess the OE.
Intelligence, as the synthesis of quantitative analysis and qualitative judgment is subject to competing interpretation.
Intelligence includes the organizations, capabilities, and processes involved in the collection, processing, exploitation, analysis, and dissemination of information or finished intelligence.
Intelligence, however, is not an end in itself. To increase the operational relevance of intelligence, intelligence planners and managers should anticipate consumer needs. Thus, an examination of whether intelligence is effective or influential not only depends on the intelligence organizations, processes, and products, but must also examine users’ intelligence needs.
Intelligence products provide users with the information that has been collected and analyzed based on their requirements. It is important to remember that because the OE is dynamic, intelligence is a continuous activity.
Intelligence – Goals Before Data
What systems, data, and other digital assets must be protected?
How do you anticipate threat intelligence will help protect those assets?
With which specific tactics are you expecting intelligence to help?
Intelligence – Framework Tools
Collecting: Ingesting threat data from the right sources.
Processing: Turning the data into useful information.
Analyzing: Turning the information into actionable intelligence.
Intelligence – Defined
Threat intelligence is the output of analysis based on identification, collection, and enrichment of relevant data and information.
Always keep quantifiable business objectives in mind, and avoid producing intelligence “just in case.”
Threat intelligence falls into two categories. Operational intelligence is produced by computers, whereas strategic intelligence is produced by human analysts.
The two types of threat intelligence are heavily interdependent, and both rely on a skilled and experienced human analyst to develop and maintain them.
Intelligence Planning
Intelligence Planning (IP) occurs continuously while intelligence collection and production plans are updated as a result of previous requirements being satisfied and new requirements being identified.
A conceptual model of the intelligence process
Planning and Direction.
Definition: Planning and Direction. In intelligence usage, the determination of intelligence requirements, development of appropriate intelligence architecture, preparation of a collection plan, issuance of orders and requests to information collection agencies.
IP and direction is best understood as the development of intelligence plans and the continuous management of their execution.
Planning and direction activities include, but are not limited to:
the identification and prioritization of intelligence requirements;
the development of concepts of intelligence operations and architectures required to support the action or task;
tasking subordinate intelligence elements for the collection of information or the production of finished intelligence;
submitting requests for additional capabilities to higher review;
and submitting requests for collection, exploitation, or all-source production support to external, supporting intelligence entities.
Intelligence Requirements and Information Requirements Planning
Categories of Intelligence Products:
Warning; Current; General; Target; Scientific Technical; Counterintelligence; Estimative; Identity
- Warning intelligence
- Current intelligence
- General intelligence
- Target intelligence
- Scientific and technical intelligence
- Counterintelligence
- Estimative intelligence
- Identity intelligence
Intelligence Requirements and Information Requirements Planning
Levels of Intelligence:
Strategic; Operational; Tactical
Strategic – Senior Leaders; Managers
Assist in developing strategy and policy.
Monitor the international or global situation.
Assist in developing plans.
Assist in determining major systems and structure requirements.
Support the conduct of strategic operations.
Operational – Senior Leaders; Managers
Focus on capabilities and intentions of threats and vulnerabilities
Analyze the operational environment.
Identify adversary centers of gravity and critical vulnerabilities.
Monitor events in the areas of interest.
Tactical – Managers
Support the planning and conduct of joint campaigns or efforts.
Support planning and the execution of attacks, defense, engagements, and other joint force activities.
Provide information on imminent threats and changes in the operational environment.
Provide obstacle intelligence.
Intelligence Requirements and Information Requirements Planning
Principles of Joint Intelligence:
Perspective; Synchronization; Integrity; Effort Singularity; Prioritization; Excellence; Prediction; Agility; Collaboration; Fusion
- Perspective (Think like the adversary.)
- Synchronization (Synchronize intelligence with plans and operations.)
- Integrity (Remain intellectually honest.)
- Unity of Effort (Cooperate to achieve a common end state.)
- Prioritization (Prioritize requirements based on authoritative guidance.)
- Excellence (Strive to achieve the highest standards of quality.)
- Prediction (Accept the risk of predicting adversary intentions.)
- Agility (Remain flexible and adapt to changing situations.)
- Collaboration (Leverage expertise of diverse analytic resources.)
- Fusion (Exploit all sources of information and intelligence.)
Intelligence Requirements and Information Requirements Planning
Attributes of Intelligence Excellence:
Anticipatory; Timely; Accurate; Usable; Complete; Relevant; Objective; Available
- Anticipatory
- Timely
- Accurate
- Usable
- Complete
- Relevant
- Objective
- Available
Intelligence Requirements and Information Requirements Planning
Principles for Interorganizational Intelligence Collaboration:
- Establish strong relationship networks.
- Build mutual trust and respect for colleagues.
- Share a common vision.
- Minimize territorial issues.
- Establish continuous communication.
- Eliminate impediments.
Intelligence: Relationship of Data Information and Intelligence
U.S. Department of Defense’s “Joint Publication 2-0: Joint Intelligence”
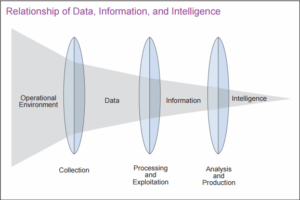
Data Information Intelligence
“Tell me what you know…tell me what you don’t know…tell me what you think—always distinguish which is which.”
General Colin Powell, US Army
Guidance to Joint Staff J-2 on 13 November 1992
Chairman of the Joint Chiefs of Staff, 1989-1993
Threat Intelligence, Information, Data: Critical Differences
There is a difference between threat data, information, and intelligence; understanding the difference is essential to getting the most out of your threat intelligence platform. The progress from data to information to intelligence, reduces the volume of outputs while the value of those outputs simultaneously increases.
Threat intelligence platforms produce data and information, which human analysts must then use to produce actionable threat intelligence. A computer can never produce threat intelligence, but humans are unsuited to the task of collecting and processing huge volumes of threat data.
Action must always be the end goal. Threat intelligence is useless unless it can be used to improve action, in this case; cyber security action.
Most organizations assume that if they buy a threat intelligence platform it will do everything for them – that isn’t the case – there are critical differences between threat data, information, and intelligence, and skilled analysts define the transition from one to the next.
The main differences between data, information, and intelligence come in two forms: volume, and usability.
Data is typically available in huge volumes, and describes individual and unarguable facts. Details of individual connection requests are an excellent example of data, because they’re simple statements of fact and aren’t open to discussion.
Information is produced when a series of raw data points are combined to answer a simple question; although this is a far more useful output than the raw data, it still doesn’t directly inform a specific action.
Intelligence takes this process a stage further by interrogating data and information to tell a story (a forecast, for example) that can be used to inform decision making. Crucially, intelligence never answers a simple question, rather it paints a picture that can be used to help people answer much more complicated questions. Intelligence may not directly answer a specific question, but it does aid in the decision-making process.
Threat Intelligence Platforms don’t actually produce Threat Intelligence: To produce a small but steady stream of actionable threat intelligence, massive quantities of data are required. Simple threat intelligence platforms are able to consume and organize threat data on a large scale, which makes the job of your analysts far easier, and their outputs more useful.
An important function of threat intelligence products is to organize threats according to their potential to damage an organization. This is where the very best providers differentiate themselves from the rest of the pack: They’re able to prioritize threats automatically, so human analysts can focus their efforts on the most important threat data or information first. Because of the big data issues described above, having a tool that can prioritize threats is essential. If your analysts are digging through every single threat manually, you’ll find that many urgent threats aren’t identified until after the fact. The process of combining and organizing threat data into threat information is fundamental to the prioritization process.
When it comes to threat intelligence, action is the only thing that really counts. There’s absolutely no value in possessing threat data, information, or intelligence unless you use it to improve your security program or defend against an incoming attack.
Tags: MG Strategy+ Corporate,MG Strategy+ Security Intelligence,MGS+ Reports,MGS+ Security Data Services,Threat Intelligence,Threat Intelligence Data,Threat Intelligence Information,Threat Intelligence Platforms,